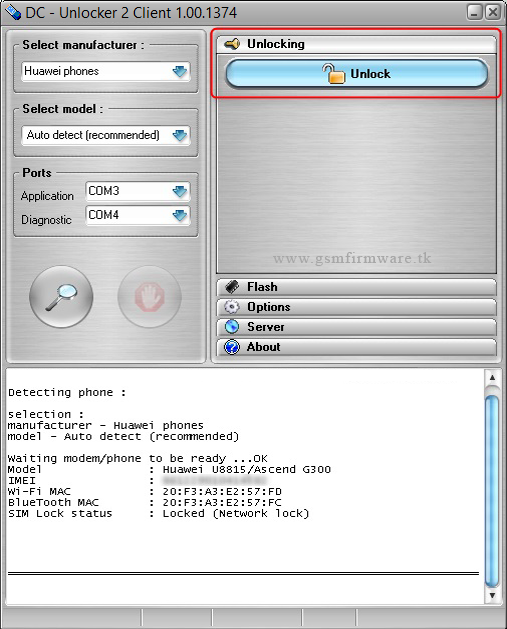
Working Username And Password For Dc Unlocker Client Cracked Full ^NEW^ ⛔
Working Username And Password For Dc Unlocker Client Cracked Full
the next step is to lock down the domain administrator’s computer, because this is the one that has the stored credentials of every user within the domain. if the domain administrator is compromised, any user on the domain could be compromised and the remaining computers are still open to attack.
the next step is to set up a new domain controller as a holding point for all the credentials, also known as the delegation server. the domain administrator can no longer log into any user’s computer, but they can still access the holding server and copy the credentials.
the credentials are then cleaned up by marking them as bad and changing them so they can’t be used anymore. in this way, a hacker would have to know the username, password, and domain that was being used by the victims in order to continue using their stolen credentials.
the next thing to consider are protocols that can be used to build credentials. these are terms that describe a piece of information that can be used to provide authentication, in order to allow access. these protocols are also known as authentication methods.
hashing is a type of technique that involves using a mathematical algorithm to map the plaintext to a form where only the owner can decipher the message, without revealing the original text that was intended to be protected. these are widely used in digital security, since they are the basis of public-key cryptographic algorithms and digital certificates, especially x.509.
for example, a common method of storing usernames and passwords is using a file that contains a list of usernames and passwords. the idea is that the file is stored on the domain administrator’s computer, and the credentials are mapped to the proper user account.
then, the system needs to validate the credentials. once the credentials are set up, the users will be able to log in, but when the system attempts to validate the password, the credentials wouldn’t be valid and the user is denied access.
digital signatures can be used as a means of verifying signatures on documents or files. a digital signature is used to represent the creator of a given document or file, because it is the original creator’s private key.
the previous working username and password for dc unlocker client cracked full shows that our hack’s success was due to the use of mitm service. we need to have a username and a password that our hacker can change without us knowing, we need it for the request to the socks proxy in order to send our traffic through the hacker proxy and intercept the traffic. we will be using our non-existant username and our non-existant password
the attacker is sending requests to the socks proxy using the non-existant username and non-existant password that we have. thus, by leveraging mitm we intercept those requests, and we immediately redirect those requests through the hacker proxy. but what does the attacker really have access to?
the attacker will have the option to manage the web server. if he allows file changes to modify the application files on his server, he will have complete control of all the files on the server. that is, he will be able to change any text file, any php files and modify any configuration file. if he added account manager, he will also have the login to the application. with these two tools, he will have complete control of this server, and he will be able to fully crack our login credentials.
5ec8ef588b
https://oualie.dev/wp-content/uploads/2022/11/ChangedOST_Download_VERIFIED_Apunkagames.pdf
http://classacteventseurope.com/wp-content/uploads/2022/11/ulrimel.pdf
https://wanderfuls.com/wp-content/uploads/2022/11/yabalec.pdf
http://steamworksedmonton.com/wp-content/uploads/Global_Mapper_20_Crack_With_Keygen_Win_Mac_Full_Download_REPACK.pdf
https://superstitionsar.org/shri-jyoti-star-6-crack-full/
https://knowthycountry.com/wp-content/uploads/2022/11/januiphi.pdf
https://carolwestfineart.com/wp-content/uploads/2022/11/jaquind.pdf
https://carolwestfineart.com/wp-content/uploads/2022/11/franphi.pdf
https://meinemarkemeingesicht.de/wp-content/uploads/2022/11/talihenl.pdf
https://believewedding.com/wp-content/uploads/2022/11/CIRCAD_V6_OmniGlyphV6_Full.pdf
https://witfoodx.com/radar-10-5-homeopathic-software-free-download-verified/
https://luxepropertiesnw.com/wp-content/uploads/2022/11/lawak_ke_der_install_download_full_28.pdf
https://fotofables.com/jaltest-soft-crack-keygen-exclusive/
https://blu-realestate.com/?p=186176
https://lavavajillasportatiles.com/josue-de-castro-pra-sempre-teu-pb-exclusive/
http://www.kiwitravellers2017.com/wp-content/uploads/2022/11/3d_Ripper_Dx_Version_17_FULL_Download_1.pdf
https://konnektion.com/advert/igo-primo-2-4-6-europe-torrent-full/
https://9escorts.com/advert/igo-primo-v9-6-7-235654-torrents-download-link/
https://www.impactunlimited.co.za/advert/samsung-2g-tool-v-3-5-0035-2/
https://www.loolooherbal.in/wp-content/uploads/2022/11/talehary.pdf